Kubernets
简介
kubeadm-单节点-ubuntu
kubeadm-高可用集群-ubuntu
资源管理
Namespace
Pod
Pod控制器
Pod生命周期
Pod调度
Label
Service
数据存储
安全认证
DashBoard
kubeadm-单节点-centos
kubeadm-高可用集群-centos
本文档使用 MrDoc 发布
-
+
首页
Service
# 简介 利用Deployment来创建一组Pod来提供具有高可用性的服务,虽然每个Pod都会分配一个单独的Pod的IP地址,但是却存在如下的问题: - Pod的IP会随着Pod的重建产生变化。 - Pod的IP仅仅是集群内部可见的虚拟的IP,外部无法访问。 这样对于访问这个服务带来了难度,因此,kubernetes设计了Service来解决这个问题。 Service可以看做是一组同类的Pod对外的访问接口,借助Service,应用可以方便的实现服务发现和负载均衡。 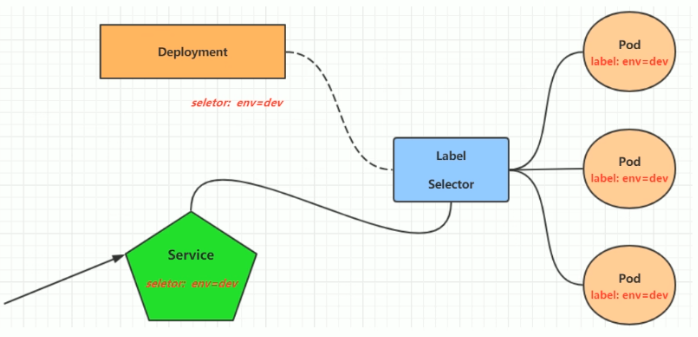 **Service在很多情况下只是一个概念,真正起作用的其实是kube-proxy服务进程** 每个Node节点上都运行了一个kube-proxy的服务进程,当创建Service的时候会通过API Server向etcd写入创建的Service的信息,而kube-proxy会基于监听的机制发现这种Service的变化,然后它会将最新的Service信息转换为对应的访问规则。 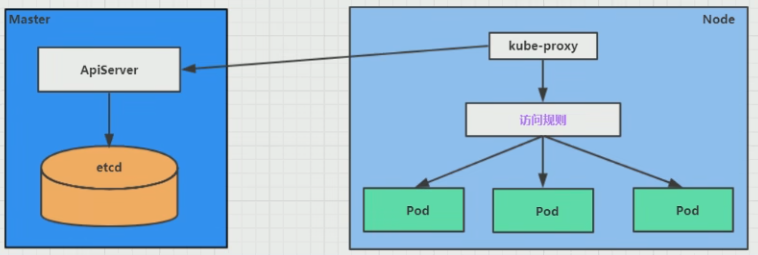 # kube-proxy工作模式 ## userspace模式 kube-proxy会为每一个Service创建一个监听端口,发向Cluster IP的请求被iptables规则重定向到kube-proxy监听的端口上 kube-proxy根据LB算法(负载均衡算法)选择一个提供服务的Pod并和其建立连接,以便将请求转发到Pod上 kube-proxy充当了一个四层负载均衡器的角色。由于kube-proxy运行在userspace中,在进行转发处理的时候会增加内核和用户空间之间的数据拷贝,虽然比较稳定,但是效率非常低下 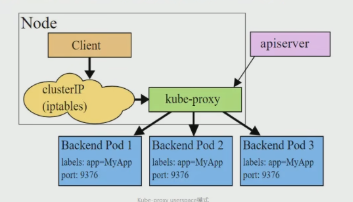 ## iptables模式 kube-proxy为Service后端的每个Pod创建对应的iptables规则,直接将发向Cluster IP的请求重定向到一个Pod的IP上 kube-proxy不承担四层负载均衡器的角色,只负责创建iptables规则 该模式的优点在于较userspace模式效率更高,但是不能提供灵活的LB策略,当后端Pod不可用的时候无法进行重试 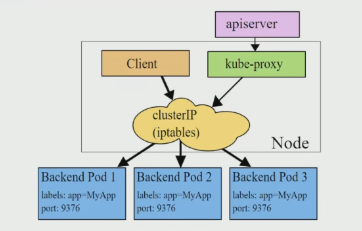 ## ipvs模式 和iptables类似,kube-proxy监控Pod的变化并创建相应的ipvs规则 ipvs相对iptables转发效率更高,除此之外,ipvs支持更多的LB算法 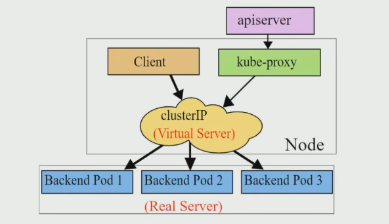 # 开启ipvs模式 (必须安装ipvs内核模块,否则会降级为iptables) 修改kube-proxy模式 ```asp kubectl edit cm kube-proxy -n kube-system ``` ```asp metricsBindAddress: "" #在""内添加ipvs字段 mode: "ipvs" nodePortAddresses: null ``` 删除老的kube-proxy重新加载 ```asp kubectl delete pod -l k8s-app=kube-proxy -n kube-system ``` 查看ipvs规则 ```asp ipvsadm -Ln ``` ```asp IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn ... TCP 10.96.0.1:443 rr -> 192.168.1.100:6443 Masq 1 0 0 ... ``` # 资源清单 ```asp apiVersion: v1 #版本 kind: Service #类型 metadata: #元数据 name: #资源名称 namespace: #命名空间 spec: #描述 selector: #标签选择器,用于确定当前Service代理那些Pod app: nginx type: NodePort #Service的类型,指定Service的访问方式 clusterIP: #虚拟服务的IP地址 sessionAffinity: #session亲和性,支持ClientIP、None两个选项,默认值为None ports: # 端口信息 - port: 3017 #Service端口 targetPort: #Pod端口 nodePort: #主机端口 --------------------------------------------------------------------------- spec.type的说明: ClusterIP: #默认值,它是kubernetes系统自动分配的虚拟IP,只能在集群内部访问 NodePort: #将Service通过指定的Node上的端口暴露给外部,通过此方法,就可以在集群外部访问服务 LoadBalancer: #使用外接负载均衡器完成到服务的负载分发,注意此模式需要外部云环境的支持 ExternalName: #把集群外部的服务引入集群内部,直接使用 ``` # 基本操作 创建pod ```asp kubectl run nginx --image=nginx --port=80 -n dev ``` 创建service指定:指定pod、svc名称、类型(内部访问:ClusterIP、外部访问:NodePort)、映射端口、指定ns ```asp kubectl expose deployment nginx --name=svc-nginx --type=NodePort --port=80 --target-port=80 -n dev ``` 查看service及pod信息 ```asp kubectl get pod,svc -n dev ``` ```asp NAME READY STATUS RESTARTS AGE pod/nginx-6d48c9bcb8-pcr4g 1/1 Running 0 92s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/svc-nginx NodePort 10.97.177.80 <none> 80:31841/TCP 63s ``` 删除svc ```asp kubectl delete svc svc-nginx -n dev ``` 删除pod ```asp kubectl delete deployment nginx -n dev ``` # 进阶使用 ## 环境准备 Deployment创建出3个Pod(注意要为Pod设置app=nginx-pod的标签) ```asp cat <<EOF> pc-deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: name: pc-deployment namespace: dev spec: replicas: 3 selector: matchLabels: app: nginx-pod template: metadata: labels: app: nginx-pod spec: containers: - name: nginx image: nginx:1.17.1 ports: - containerPort: 80 EOF ``` 运行 ```asp kubectl create -f pc-deployment.yaml ``` 查看 ```asp kubectl get pod -n dev -o wide ``` ```asp NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES pc-deployment-7d7dd5499b-ztwkc 1/1 Running 0 9s 10.244.166.137 node1 <none> <none> pc-deployment-7d7dd5499b-n2pk8 1/1 Running 0 9s 10.244.104.16 node2 <none> <none> pc-deployment-7d7dd5499b-m5bwn 1/1 Running 0 9s 10.244.135.11 node3 <none> <none> ``` 修改3个Nginx的主页 ```asp kubectl exec -it pc-deployment-7d7dd5499b-ztwkc -c nginx -n dev /bin/sh echo "node-1-10.244.166.137" > /usr/share/nginx/html/index.html && exit ``` ```asp kubectl exec -it pc-deployment-7d7dd5499b-n2pk8 -c nginx -n dev /bin/sh echo "node-2-10.244.104.16" > /usr/share/nginx/html/index.html && exit ``` ```asp kubectl exec -it pc-deployment-7d7dd5499b-m5bwn -c nginx -n dev /bin/sh echo "node-3-10.244.135.11" > /usr/share/nginx/html/index.html && exit ``` 访问测试 ```asp curl 10.244.166.137 curl 10.244.104.16 curl 10.244.135.11 ``` ## ClusterIP 默认值,kubernetes系统自动分配的虚拟IP,只能在集群内部访问 创建service-clusterip.yaml ```asp cat <<EOF> service-clusterip.yaml apiVersion: v1 kind: Service metadata: name: service-clusterip namespace: dev spec: #sessionAffinity: ClientIP #启用亲和性后,第一个为该用户提供服务器的pod将会一直为该用户提供服务 selector: app: nginx-pod clusterIP: 10.97.97.97 #service的IP地址,如果不写,默认会生成一个 type: ClusterIP ports: - port: 80 #Service端口 targetPort: 80 #Pod的端口 EOF ``` 运行 ```asp kubectl create -f service-clusterip.yaml ``` 查看svc和pod ```asp kubectl get svc,pod -n dev ``` ```asp NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/service-clusterip ClusterIP 10.97.97.97 <none> 80/TCP 15s NAME READY STATUS RESTARTS AGE pod/pc-deployment-7d7dd5499b-9sppl 1/1 Running 0 44m pod/pc-deployment-7d7dd5499b-knrmq 1/1 Running 0 44m pod/pc-deployment-7d7dd5499b-prfkb 1/1 Running 0 44m ``` 查看svc详细信息 ```asp kubectl describe svc service-clusterip -n dev ``` ```asp Name: service-clusterip Namespace: dev Labels: <none> Annotations: <none> Selector: app=nginx-pod Type: ClusterIP IP: 10.97.97.97 Port: <unset> 80/TCP TargetPort: 80/TCP Endpoints: 10.244.104.4:80,10.244.135.8:80,10.244.166.131:80 Session Affinity: None Events: <none> ``` 查看ipvs规则 ```asp ipvsadm -Ln ``` ```asp IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn ... TCP 10.97.97.97:80 rr persistent 10800 #亲生性生效:persistent会话保持、10800保持时间 -> 10.244.104.4:80 Masq 1 0 0 -> 10.244.135.8:80 Masq 1 0 0 -> 10.244.166.131:80 Masq 1 0 0 ... ``` 访问svc测试(可以看到svc默认以轮询的方式将请求转发给3个pod) ```asp while true;do curl 10.97.97.97; sleep 1; done; ``` ```asp node-3-10.244.135.8 node-2-10.244.104.4 node-1-10.244.166.131 node-3-10.244.135.8 node-2-10.244.104.4 node-1-10.244.166.131 ... ``` 删除 ```asp kubectl delete -f service-clusterip.yaml ``` ## HeadLiness 某些场景中,开发人员可能不想使用Service提供的负载均衡功能,而希望自己来控制负载均衡策略,针对这种情况,kubernetes提供了HeadLinesss Service,这类Service不会分配Cluster IP,如果想要访问Service,只能通过Service的域名进行查询。 创建service-headliness.yaml ```asp cat <<EOF> service-headliness.yaml apiVersion: v1 kind: Service metadata: name: service-headliness namespace: dev spec: selector: app: nginx-pod clusterIP: None #设置为None即可创建headliness类型Service type: ClusterIP ports: - port: 80 #Service端口 targetPort: 80 #Pod的端口 EOF ``` 运行 ```asp kubectl create -f service-headliness.yaml ``` 查看 ```asp kubectl get -f service-headliness.yaml ``` 查看svc ```asp kubectl get svc,pod -n dev ``` ```asp NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service-headliness ClusterIP None <none> 80/TCP 4s ``` 查看当前pod的域名服务器ip ```asp kubectl exec -it pc-deployment-7d7dd5499b-ztwkc -c nginx -n dev /bin/sh cat /etc/resolv.conf && exit ``` 下载测试工具 ```asp yum -y install bind-utils ``` 解析DNS会出现三个pod对应的IP信息 ```asp dig @10.96.0.10 service-headliness.dev.svc.cluster.local ``` ```asp ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.16 <<>> @10.96.0.10 service-headliness.dev.svc.cluster.local ... ;; ANSWER SECTION: service-headliness.dev.svc.cluster.local. 30 IN A 10.244.166.131 service-headliness.dev.svc.cluster.local. 30 IN A 10.244.135.8 service-headliness.dev.svc.cluster.local. 30 IN A 10.244.104.10 ... ``` 删除 ```asp kubectl delete -f service-headliness.yaml ``` ## NodePort NodePort的工作原理就是将Service的端口映射到Node的一个端口上,然后就可以通过node-ip:nodeport来访问service 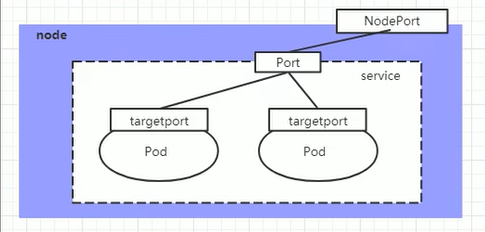 创建service-nodeport.yaml ```asp cat <<EOF> service-nodeport.yaml apiVersion: v1 kind: Service metadata: name: service-nodeport namespace: dev spec: selector: app: nginx-pod type: NodePort #Service类型 ports: - port: 80 targetPort: 80 nodePort: 30000 #指定绑定的node的端口(默认取值范围是30000~32767)不指定默认分配 EOF ``` 运行 ```asp kubectl create -f service-nodeport.yaml ``` 查看 ```asp kubectl get svc -n dev ``` ```asp NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service-headliness ClusterIP None <none> 80/TCP 18m service-nodeport NodePort 10.111.134.135 <none> 80:30000/TCP 29s ``` 访问测试 ```asp curl 192.168.1.100:30000 curl 192.168.1.101:30000 curl 192.168.1.102:30000 curl 192.168.1.103:30000 ``` 删除 ```asp kubectl delete -f service-nodeport.yaml ``` ## LoadBalancer 和NodePort很相似,目的都是向外部暴露一个端口,区别在于LoadBalancer会在集群的外部再来做一个负载均衡设备,而这个设备需要外部环境的支持,外部服务发送到这个设备上的请求,会被设备负载之后转发到集群中 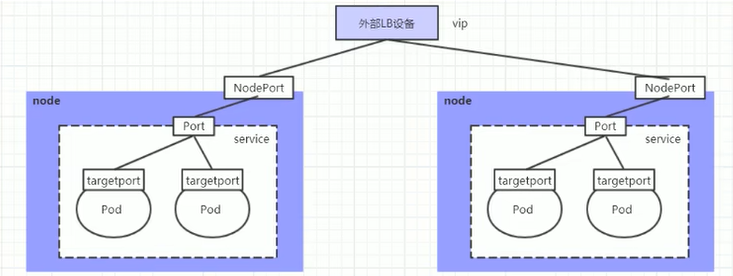 ## ExternalName 用于引入集群外部的服务,通过externalName属性指定一个服务的地址,然后在集群内部访问此Service就可以访问到外部的服务了。 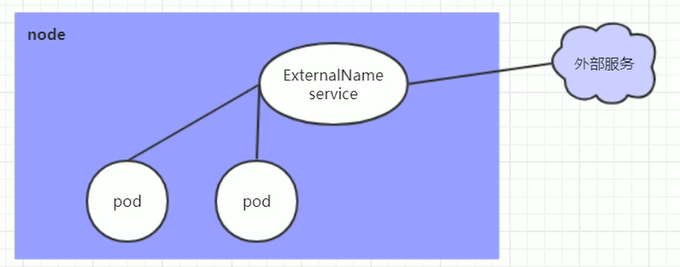 ```asp cat <<EOF> service-externalname.yaml apiVersion: v1 kind: Service metadata: name: service-externalname namespace: dev spec: type: ExternalName #Service类型 externalName: www.baidu.com #域名IP均可 EOF ``` 运行 ```asp kubectl create -f service-externalname.yaml ``` 查看 ```asp kubectl get -f service-externalname.yaml ``` 查看域名服务器会出现百度的IP信息 ```asp dig @10.96.0.10 service-externalname.dev.svc.cluster.local ``` ```asp ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.16 <<>> @10.96.0.10 service-externalname.dev.svc.cluster.local ... ;; ANSWER SECTION: service-externalname.dev.svc.cluster.local. 18 IN CNAME www.baidu.com. www.baidu.com. 18 IN CNAME www.a.shifen.com. www.a.shifen.com. 18 IN A 39.156.66.18 www.a.shifen.com. 18 IN A 39.156.66.14 ... ``` 删除svc ```asp kubectl delete -f service-externalname.yaml ``` 删除pod ```asp kubectl delete -f pc-deployment.yaml ``` # Ingress 上面讲到的Service对集群之外暴露服务的两种方式(NodePort、LoadBalancer)都有一定缺点: - NodePort方式的缺点是会占用很多集群机器的端口,那么当集群服务变多的时候,这个缺点就愈发明显 - LoadBalancer的缺点是每个Service都需要一个LB,浪费,麻烦,并且需要kubernetes之外的设备的支持 基于这种现状,kubernetes提供了Ingress资源对象,Ingress只需要一个NodePort或者一个LB就可以满足暴露多个Service的需求 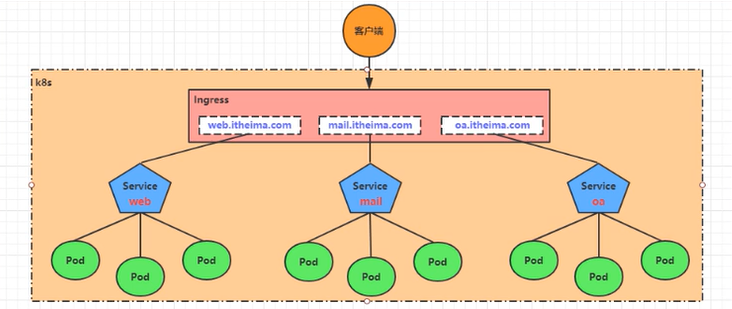 Ingress相当于一个七层的负载均衡器,是kubernetes对反向代理的一个抽象,它的工作原理类似于Nginx Ingress建立了诸多映射规则,Ingress Controller通过监听这些配置规则并转化为Nginx的反向代理配置,然后对外提供服务 - Ingress:是K8s中的一个对象,作用是定义请求如何转发到Service的规则 - Ingress Controller:具体实现反向代理及负载均衡的程序,对Ingress定义的规则进行解析,根据配置的规则来实现请求转发 Ingress(以Nginx为例)的工作原理: - 用户编写Ingress规则,说明那个域名对应kubernetes集群中的那个Service。 - Ingress控制器动态感知Ingress服务规则的变化,然后生成一段对应的Nginx的反向代理配置。 - Ingress控制器会将生成的Nginx配置写入到一个运行着的Nginx服务中,并动态更新。 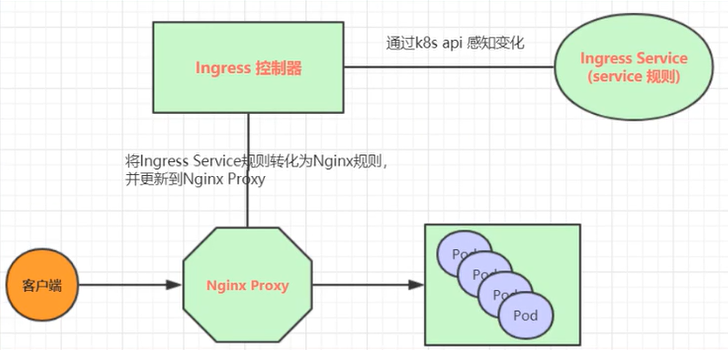 ## 初始化环境 创建文件夹进入 ```asp mkdir -pv /home/k8s && cd /home/k8s ``` 下载ingress-nginx插件,对应版本nginx-0.30.0;官方下载:[mandatory.yaml](https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/mandatory.yaml "mandatory.yaml")、[service-nodeport.yaml](https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/provider/baremetal/service-nodeport.yaml "service-nodeport.yaml") ```asp wget https://pan.cddone.com/d/package/tar/k8s/mandatory.yaml ``` 修改api允许暴漏80和443端口 ```asp vim /etc/kubernetes/manifests/kube-apiserver.yaml ``` ```asp ... - --service-cluster-ip-range=10.96.0.0/12 - --service-node-port-range=1-65535 #新增 - --tls-cert-file=/etc/kubernetes/pki/apiserver.crt ... ``` 重启api ```asp systemctl daemon-reload systemctl restart kubelet ``` 创建service-nodeport.yaml ```asp cat <<EOF> service-nodeport.yaml apiVersion: v1 kind: Service metadata: name: ingress-nginx namespace: ingress-nginx labels: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/part-of: ingress-nginx spec: type: NodePort ports: - name: http port: 80 targetPort: 80 nodePort: 80 protocol: TCP - name: https port: 443 targetPort: 443 nodePort: 443 protocol: TCP selector: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/part-of: ingress-nginx EOF ``` 运行 ```asp kubectl apply -f ./ ``` 查看ingress-nginx ```asp watch kubectl get pod -n ingress-nginx ``` ```asp NAME READY STATUS RESTARTS AGE nginx-ingress-controller-5bb8fb4bb6-jm2rt 1/1 Running 0 4m49s ``` 查看svc ```asp kubectl get svc -n ingress-nginx ``` ```asp NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE ingress-nginx NodePort 10.108.147.214 <none> 80:80/TCP,443:443/TCP 60m ``` 创建tomcat-nginx.yaml 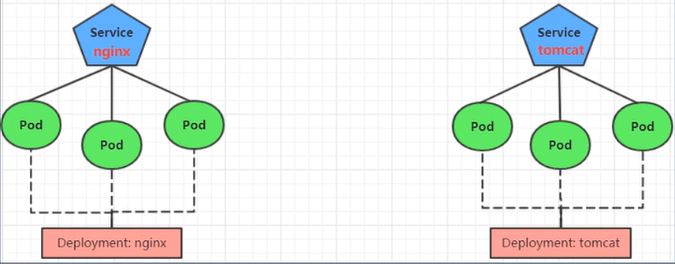 ```asp cat <<EOF> tomcat-nginx.yaml apiVersion: apps/v1 kind: Deployment metadata: name: nginx-deployment namespace: dev spec: replicas: 3 selector: matchLabels: app: nginx-pod template: metadata: labels: app: nginx-pod spec: containers: - name: nginx image: nginx:1.17.1 ports: - containerPort: 80 --- apiVersion: apps/v1 kind: Deployment metadata: name: tomcat-deployment namespace: dev spec: replicas: 3 selector: matchLabels: app: tomcat-pod template: metadata: labels: app: tomcat-pod spec: containers: - name: tomcat image: tomcat:8.5-jre10-slim ports: - containerPort: 8080 --- apiVersion: v1 kind: Service metadata: name: nginx-service namespace: dev spec: selector: app: nginx-pod clusterIP: None type: ClusterIP ports: - port: 80 targetPort: 80 --- apiVersion: v1 kind: Service metadata: name: tomcat-service namespace: dev spec: selector: app: tomcat-pod clusterIP: None type: ClusterIP ports: - port: 8080 targetPort: 8080 EOF ``` 运行 ```asp kubectl create -f tomcat-nginx.yaml ``` 查看svc和pod ```asp kubectl get svc,pod -n dev -o wide ``` ```asp NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR service/nginx-service ClusterIP None <none> 80/TCP 13s app=nginx-pod service/tomcat-service ClusterIP None <none> 8080/TCP 13s app=tomcat-pod NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES pod/nginx-deployment-7d7dd5499b-8hh8x 1/1 Running 0 13s 10.244.135.10 node3 <none> <none> pod/nginx-deployment-7d7dd5499b-njrv5 1/1 Running 0 13s 10.244.104.12 node2 <none> <none> pod/nginx-deployment-7d7dd5499b-xqtwh 1/1 Running 0 13s 10.244.166.132 node1 <none> <none> pod/tomcat-deployment-7d5fcd4756-69psn 1/1 Running 0 13s 10.244.104.13 node2 <none> <none> pod/tomcat-deployment-7d5fcd4756-drsnx 1/1 Running 0 13s 10.244.135.9 node3 <none> <none> pod/tomcat-deployment-7d5fcd4756-gpd2d 1/1 Running 0 13s 10.244.166.133 node1 <none> <none> ``` win宿主机添加测试域名的解析记录:C:\Windows\System32\drivers\etc ```asp 192.168.1.100 nginx.done.com 192.168.1.101 nginx.done.com 192.168.1.102 nginx.done.com 192.168.1.103 nginx.done.com 192.168.1.100 tomcat.done.com 192.168.1.101 tomcat.done.com 192.168.1.102 tomcat.done.com 192.168.1.103 tomcat.done.com ``` ## Ingress-http 创建ingress-http.yaml ```asp cat <<EOF> ingress-http.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: ingress-http namespace: dev spec: rules: #规则 - host: k8s.cddone.com #基于域名 http: paths: - path: / #访问根目录 backend: serviceName: nginx-service #转到nginx的svc servicePort: 80 - host: k8ss.cddone.com #基于域名 http: paths: - path: / #访问根目录 backend: serviceName: tomcat-service #转到tomcat的svc servicePort: 8080 EOF ``` 运行 ```asp kubectl create -f ingress-http.yaml ``` 查看 ```asp kubectl get -f ingress-http.yaml ``` ```asp NAME CLASS HOSTS ADDRESS PORTS AGE ingress-http <none> nginx.done.com,tomcat.done.com 80 12s ``` 查看详细信息 ```asp kubectl describe -f ingress-http.yaml ``` ```asp Name: ingress-http Namespace: dev Address: 10.107.69.216 Default backend: default-http-backend:80 (<none>) Rules: Host Path Backends ---- ---- -------- nginx.done.com / nginx-service:80 (10.244.104.2:80,10.244.135.5:80,10.244.166.129:80) tomcat.done.com / tomcat-service:8080 (10.244.104.3:8080,10.244.135.6:8080,10.244.166.130:8080) Annotations: Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 53s nginx-ingress-controller Ingress dev/ingress-http Normal UPDATE 8s nginx-ingress-controller Ingress dev/ingress-http ``` 测试 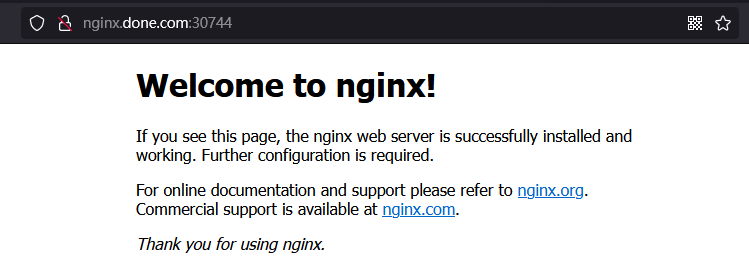 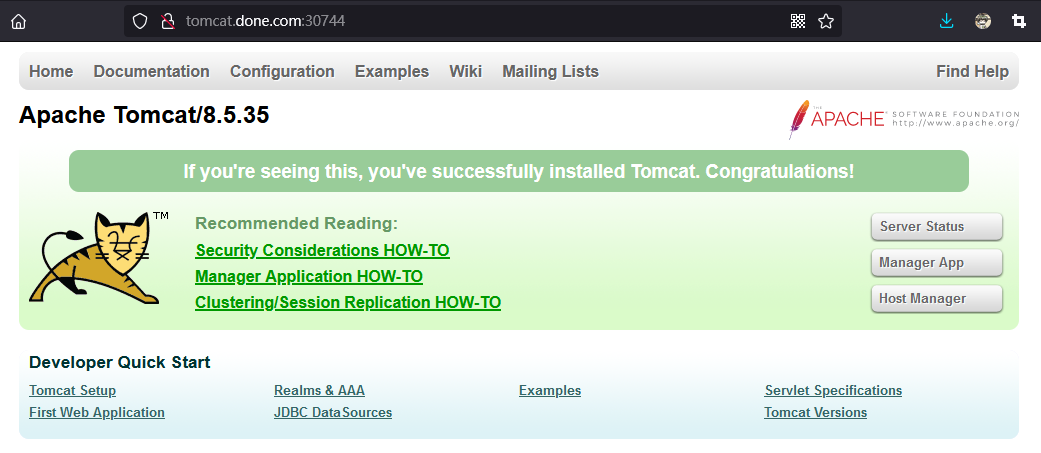 删除 ```asp kubectl delete -f ingress-http.yaml ``` ## Ingress-https 导入域名证书 ```asp kubectl create secret tls cddone.tls --key cddone.key --cert cddone.crt -n dev ``` 查看证书 ```asp kubectl get secrets -n dev ``` ```asp NAME TYPE DATA AGE cddone.tls kubernetes.io/tls 2 8s default-token-52xt4 kubernetes.io/service-account-token 3 8h ``` 创建ingress-https.yaml ```asp cat <<EOF> ingress-https.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: ingress-https namespace: dev spec: tls: - hosts: - k8s.cddone.com - k8ss.cddone.com secretName: cddone.tls #指定秘钥 rules: - host: k8s.cddone.com http: paths: - path: / backend: serviceName: nginx-service servicePort: 80 - host: k8ss.cddone.com http: paths: - path: / backend: serviceName: tomcat-service servicePort: 8080 EOF ``` 运行 ```asp kubectl create -f ingress-https.yaml ``` 查看 ```asp kubectl get ing -n dev ``` ```asp NAME CLASS HOSTS ADDRESS PORTS AGE ingress-https <none> nginx.done.com,tomcat.done.com 80, 443 4s ``` 查看详细信息 ```asp kubectl describe -f ingress-https.yaml ``` ```asp Name: ingress-https Namespace: dev Address: 10.107.69.216 Default backend: default-http-backend:80 (<none>) TLS: tls-secret terminates nginx.done.com,tomcat.done.com Rules: Host Path Backends ---- ---- -------- nginx.done.com / nginx-service:80 (10.244.104.2:80,10.244.135.5:80,10.244.166.129:80) tomcat.done.com / tomcat-service:8080 (10.244.104.3:8080,10.244.135.6:8080,10.244.166.130:8080) Annotations: Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 2m20s nginx-ingress-controller Ingress dev/ingress-https Normal UPDATE 2m9s nginx-ingress-controller Ingress dev/ingress-https ``` 测试 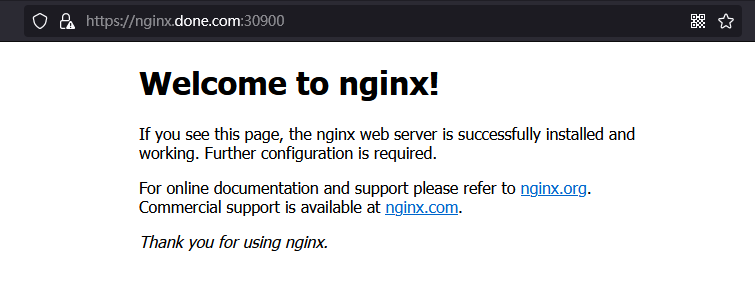 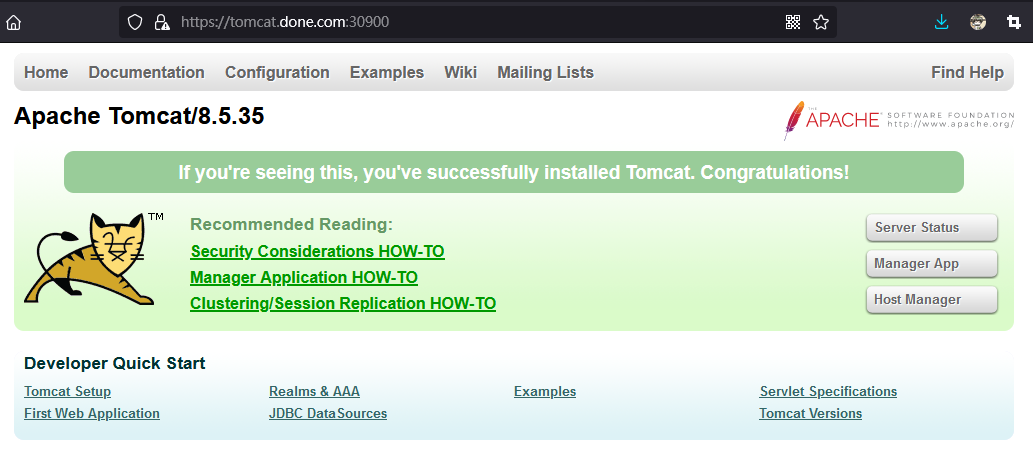 删除 ```asp kubectl delete -f ./ ```
done
2024年7月10日 14:49
转发文档
收藏文档
上一篇
下一篇
手机扫码
复制链接
手机扫一扫转发分享
复制链接
Markdown文件
分享
链接
类型
密码
更新密码